Update: SinVR says it has fixed the issue that was highlighted by the security firm Digital Interruption:

“Digital Interruption gave us ample warning before posting their finding and we fixed the issue as soon as it was revealed to us,” a spokesperson for the company told Alphr. “We are in contact with them and they confirmed that the outlined security hole was closed. Altogether, it has been a tremendous learning experience, which will serve to enhance our security and we are glad that it was conducted ethically.
“Moving forward, we are confident in our ability to stop similar attacks and will keep using a professional security service to audit our system. We are making sure that all ‘back door’ intrusions are fully consensual.”
Digital Interruption confirmed the fix in a tweet:
The original story continues below:
Around 20,000 people have had their data exposed following a security leak at adult VR app SinVR.
SinVR is a pornographic virtual-reality game offering users their own “private dungeon”. As Security Ledger reports, tens of thousands of customer records were uncovered by UK security firm Digital Interruption, which found a high-risk vulnerability in the SinVR application. This led the ethical hackers to the names, email addresses and device names for everyone with a SinVR account, as well as anyone who paid for content using PayPal.
“Not only could an attacker use this to perform social engineering attacks, but, due to the nature of the application, it is potentially quite embarrassing to have details like this leaked,” writes Digital Interruption in a blogpost. “It is not outside the realm of possibility that some users could be blackmailed with this information.

(Credit: SinVR)
READ NEXT – Beyond Pornhub: The sex rebels reclaiming adult film
Digital Interruption discovered the vulnerability as part of a survey of adult websites. The team reverse engineered the SinVR desktop app, and came across the inconspicuously named function “downloadallcustomers”. The function couldn’t be enabled from the application itself, but by looking at how the web API worked, the researchers triggered it manually.
After being frustrated in their attempts to contact the parent company of SinVR, InVR Inc, the researchers took the step to go public with their findings – which they did last week, although not without censoring personal details in their screenshots. They claim it would be possible for an attacker to download a full list of SinVR users, although password and credit card details are not part of the data dump.
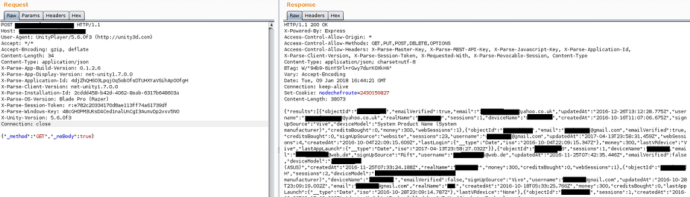
(Above: Censored image of leaked data obtained by Digital Disruption. Credit: Digital Interruption)
The users on a site like SinVR may be small compared to those on the infidelity dating site Ashley Madison – which was breached in 2015 – but, as Digital Interruption notes, an attacker could similarly use the sensitive nature of the app for blackmail.
SinVR has confirmed that the problem is now fixed, praising Digitial Interruption’s work: “Altogether, it has been a tremendous learning experience, which will serve to enhance our security and we are glad that it was conducted ethically,” a spokesperson for the app said.
Disclaimer: Some pages on this site may include an affiliate link. This does not effect our editorial in any way.











